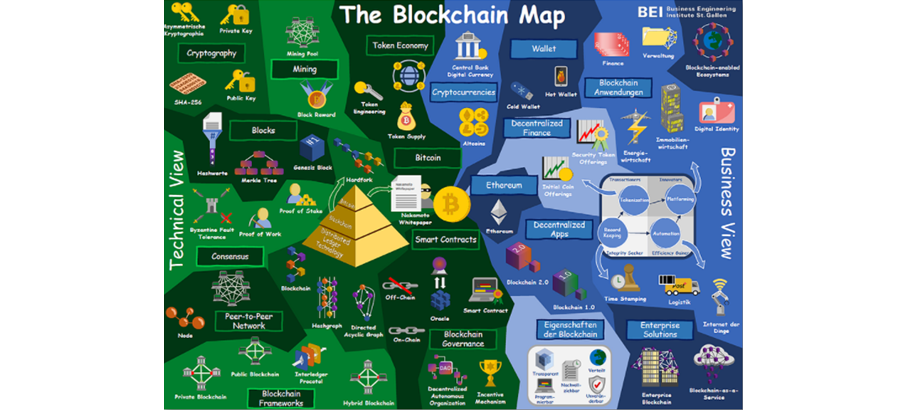
The Technical Side of the Blockchain Map
In our last blog post, “The BlockWiki – The Blockchain Explained,” we introduced the BlockWiki, a compilation of blockchain terms and research on blockchain and distributed ledger technology. One component of the BlockWiki is the Blockchain Map, which graphically depicts the technical background, various uses and functions of the technology. It is divided into two sections: technical view and business view. In this blog post, the focus will be on explaining the elements of the technical side.
Centrally located in the middle of the blockchain map is a coin with the Bitcoin logo. Bitcoin is the best-known blockchain application and one reason why the blockchain has gained so much attention in recent years. It is a cryptocurrency that is based on distributed ledger technology and does not require a central authority. New Bitcoins are not printed by a central bank, as is the case with a central currency, but are “mined“. In theory, anyone with a computer with high computing power can be a miner. The miner validates new transactions made via the blockchain, enters them in the decentralized account book and creates a hash value. A new miner is determined for each new block. In return for the computing power used for validation, the selected miner receives a certain number of Bitcoins, the so-called block reward. As a result, the number of Bitcoins increases over time. Many miners join together in mining pools to increase the chance of creating a block. The block reward is then divided among all participants in the mining pool proportionally according to computing power. The science that deals with mining and the digital representation of assets as tokens is called the token economy. In the meantime, just about everything can be represented as a token and stored in blocks.
As a prerequisite for storing sensitive data, a decentralized network must be able to guarantee secure encryption. Bitcoin uses asymmetric cryptography for this purpose. Unlike symmetric cryptography with only one key, asymmetric cryptography involves a private and a public key for each participant (private key and public key). By this logic, only the recipient can use his private key to decrypt a message encrypted with the corresponding public key. Bitcoin uses the SHA-256 algorithm for encryption. This converts data into a 256-bit code.
Once information has been encrypted and stored on a blockchain, it is unchangeable. This is guaranteed by the structure of the technology. As the name of the blockchain suggests, the structure can be thought of as a sequence of blocks that are connected like a chain. The very first block of a blockchain is called genesis block. Each block is assigned a hash value, a 64-byte numeric code. This can uniquely identify a block. In Bitcoin, it is calculated from a Merkle root, a nonce, and the hash of the previous block. The Merkle root is a numerical code which is generated from the information of the block. In the case of Bitcoin, this is all the verified transactions that have been made since the last block. The hash of the previous block is included so that the blocks are connected and tampering is virtually impossible. The nonce is a combination of numbers that is unknown and is used for the purpose of consensus. Consensus mechanisms are methods that verify values or transactions so that all participants in the network agree on the situation and can trust each other. The various mechanisms originated in the Byzantine Generals’ Problem, which describes a situation where there is difficulty in agreeing on a common goal and pursuing a unified strategy due to mistrust and physical distance – as in the case of a siege on a city by multiple army units with multiple generals. A Byzantine Fault Tolerance system therefore describes consensus building between different actors, even if they are not in the same place – as is also the case with the blockchain. In the proof-of-work mechanism, which is also used with Bitcoin, the first person to correctly solve a complex calculation problem is allowed to create the next block. In Bitcoin, a suitable eight-digit number must be found for this purpose, with which the hash value of the block begins with 17 zeros after the hashing algorithm has been carried out. This eight-digit number is called a nonce. Another approach to fulfill the consensus uses the proof-of-stake mechanism. Here, the respective miner is selected at random.
The individual computers participating in a blockchain network are called nodes. All nodes together make up the peer-to-peer network. This name also describes the most important characteristic of the network: the participants only act directly with each other and not via a higher or central authority that exerts control. Information or services can thus be exchanged among each other via the individual nodes. However, there are blockchain frameworks, that is, different architectures, where access permissions may differ. The best-known blockchain framework is the public blockchain, of which Bitcoin is an example. It is publicly accessible and can be viewed by everyone. This differs from the private blockchain. In order to set up a node in a private blockchain, you need authorization. Thus, with this framework, it is possible to exchange even sensitive data via the blockchain. For linking several blockchains, whether private or public, there are hybrid blockchains. They make it possible to transfer data across blockchains.
All frameworks have in common that the ledger of the blockchain is stored and updated in a distributed way at all participants. Thus, the blockchain belongs to the distributed ledger technology (DLT). In addition to blockchain, there are other technologies, for example, hashgraph and directed acyclic graph, which also belong to the distributed ledger technologies but are based on different data structures. Distributed ledger technologies can be used to create smart contracts. Smart contracts are computer programs that function as contracts and are stored on a distributed ledger. Thus, the agreements are immutable and can be entered into without verification from a third party. This logic of smart contracts is used to establish blockchain governance, higher-level rules of a blockchain, without a higher authority. This is the case, for example, with decentralized autonomous organizations (DAOs). In addition, smart contracts are also used in oracles. These are systems that can bring transaction data stored outside the blockchain (off-chain) onto the blockchain.
The left side of the blockchain map covers the most important terms from a technical perspective. Now it is particularly exciting to see which applications and functions are possible with the blockchain from a business perspective. This is shown on the right side of the map and will be explained in more detail in the next blog post.
- The Business Side of the Blockchain Map - 28.05.2021
- The Technical Side of the Blockchain Map - 28.05.2021
- The BlockWiki – the Blockchain Explained - 14.05.2021
