
Basics of cryptography and symmetric encryption
The amount of data generated, processed and used worldwide will increase from 64.2 zettabytes in 2020 to an estimated 180 zettabytes in 2025 (1, 2). Increasingly, products and services as well as communication processes, both business and private, are being digitized and outsourced to the Internet. With the increasing volume of data exchanged, aspects to ensure data security such as ensuring integrity, availability and also confidentiality are becoming increasingly important (3). For example, confidential, publicly exchanged information must be protected from access and manipulation by unauthorized third parties. Digital business transactions also require security mechanisms such as legally valid digital signatures. Such requirements can be provided by cryptographic processes (4). But what is cryptography anyway? To answer this question, basic mathematical concepts of cryptographic algorithms are presented below.
What is cryptography?
As a science and subgroup of cryptology, cryptography deals with the security of information, for example by encrypting data so that sensitive information can also be transmitted securely to communication partners (5). However, cryptography is by no means a phenomenon of the modern age. As early as 2000 BC, “secret” variants of common hieroglyphs existed in Egypt as early forms of cryptography (6). Until the 1970s, however, the use of cryptographic methods was limited almost exclusively to military and government purposes. It was not until the 1980s that cryptography was also widely used in the civilian sector, for example for banking and telecommunications. Today, it is hard to imagine everyday life without cryptographic applications, be it in electronic payment transactions, e-mail encryption and electronic locking of cars, but also in the communication of electronic devices in the Internet of Things and as security mechanisms within blockchain technology (6).
The aim of cryptography is to protect the confidentiality of information against unauthorized access by third parties. The exchange of information with a communication partner is particularly problematic because the communication channels used, such as the Internet, are often not secure. In such cases, it is possible for unauthorized third parties to “eavesdrop” on the communication channel and thus view or modify the information transmitted. To circumvent the difficult task of securing the entire communication channel, the transmitted information can be converted into messages that are unintelligible to outsiders, so that subsequently the exchanged messages can only be understood by authorized communication partners (7). This task is performed by cryptographic processes.
In cryptography, a fundamental distinction is made between symmetric and asymmetric methods for encrypting messages. For secure data exchange between two communication partners, both methods use keys to encrypt and decrypt a message to be exchanged (6).
Symmetric cryptography
In symmetric cryptography algorithms, both communication partners use a single secret key. The message to be exchanged, also known as plaintext, is encrypted by the sender, referred to below as Alice, and the ciphertext generated in the process is sent to the recipient, referred to below as Bob. The recipient must then decrypt the ciphertext and obtains access to the actual message (8).
There are numerous encryption algorithms that can be used to generate the ciphertext and vary greatly in complexity. The shift cipher is a possible example of a very simple, symmetric encryption method. As described above, Alice wants to send a secret text message to Bob and encrypts it with the shift cipher. For this purpose, each letter of the plaintext is replaced by another letter of the alphabet by shifting the alphabet by a certain number of digits. Alice then transmits the generated ciphertext and the secret key she uses, which corresponds to the number of positional shifts of the alphabet, to Bob. On the basis of this principle, for example, the Roman general Caesar presumably also encrypted his messages by cyclically shifting the alphabet by 3 positions (9). A is replaced by D, C by F and so on.
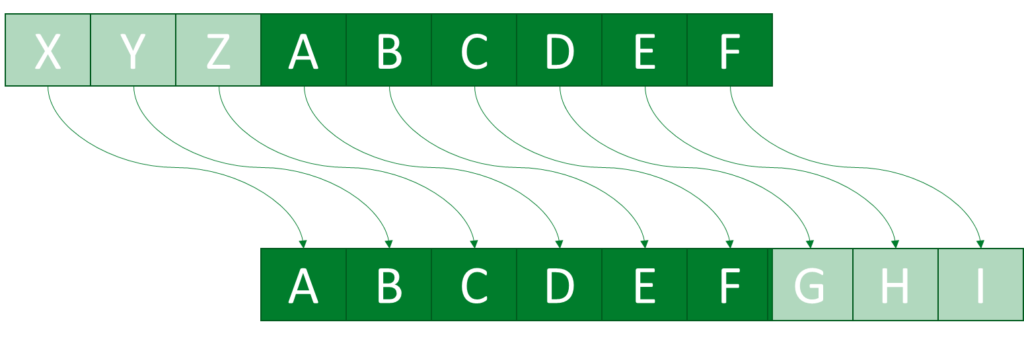
With knowledge of the ciphertext, the key used, and the underlying encryption scheme, Bob can reverse the ciphertext shift and gain access to the original message. Accordingly, in the case of the shift cipher, decrypting is the inverse operation of encrypting (6).
However, the simplicity of the described shift cipher means that the encryption can be broken relatively easily by brute force attacks, in which the solution is obtained by trying all possible results. In the shift cipher example, in the worst case, all shifts of the alphabet must be tested to decrypt a message (8). In contrast to the shift cipher described above, much more complex and correspondingly more secure symmetric encryption methods are used in practical applications, such as the Advanced Encryption Standard (AES), which is used for WLAN encryption, among other things (6, 10).
The basic assumption of symmetric cryptography is that the key used, which is to be kept secret, must be transmitted between the communication partners via a secure channel, since otherwise third parties with knowledge of the key can access the ciphertext. Accordingly, with the help of symmetric cryptography, the problem of secret message transmission is reduced only to secret key transmission. Nevertheless, Alice and Bob can communicate with each other securely as often as they like after a single secure key exchange (6).
Part 2 of this blog post deals with the concept of asymmetric cryptography methods that circumvent the described problem of secret key transmission. So check back in two weeks or follow us on LinkedIn to make sure you don’t miss anything.
Sources
- Rydning, J. (2022). Worldwide IDC Global DataSphere Forecast, 2022-2026: Enterprise Organizations Driving Most of the Data Growth. IDC. https://www.idc.com/getdoc.jsp?containerId=US49018922. Accessed on: 28.12.2022.
- Taylor, P. (2022). Volume of data/information created, captured, copied, and consumed worldwide from 2010 to 2020, with forecasts from 2021 to 2025. Statista. 08.09.2022. https://www.statista.com/statistics/871513/worldwide-data-created/. Accessed on: 28.12.2022.
- Privacy.org (2022). Data security: measures to protect data. 10/26/2022. https://www.datenschutz.org/datensicherheit-massnahmen/. Accessed on: 28.12.2022.
- Delfs, H.; Knebl, H. (2007). Introduction to Cryptography. Principles and applications. Nürnberg, Springer.
- Hellwig, D.; Karlic, G.; Huchzermeier, A. (2021). Develop your own blockchain. A practical guide to distributed ledger technology. Vallendar, New York, Springer.
- Paar, C.; Pelzl, J. (2016). Cryptography understandable. A textbook for students and users. Bochum, Springer Vieweg.
- Morbidi, D. (2018). Cryptography and encryption methods. Inpsyde. DEC. 22, 2018. https://inpsyde.com/blog/kryptografie-und-verschluesselungsverfahren/. Accessed on: 28.12.2022.
- Buchmann, J. (2016). Introduction to cryptography. 6th, revised edition. Darmstadt: Springer-Verlag
- Buchmann, J.; Bindel, N. (2016). Encryption and the limits of secrecy. In Grötschel, M.; Knobloch, E.; Schiffers, J.; Woisnitza, M.; Ziegler, G. M. Leibniz: Vision as a task. Berlin: Brandenburg Academy of Sciences, 147-159.
- Murphy, S.; Robshaw, M. J. B. (2022). Essential algebraic structure within the AES. In: CRYPTO ’02: Proceedings of the 22nd Annual International Cryptology Conference, Advances in Cryptology, pp. 1-16.
- Overview: Data value creation in companies - 09.04.2024
- Study results analyzing the needs of Swiss individuals for trusted data spaces - 11.10.2023
- The potential and development of data spaces - 31.07.2023
